
Stop. The CCPA changed recently. Many of the articles on the internet about it that I saw recently are wrong and outdated. This article is up-to-date as of its publish date.
We just received an email requesting we delete someone’s data, what do we do?
Step 1: You need to determine if you’re even subject to the CCPA. A lot of businesses aren’t. If you’re positive you aren’t, you can choose to ignore the request.
Step 2: Understand that there are both bots and misinformed individuals out there spamming CCPA requests to companies. Even if you are subject to the CCPA and received a request email your obligations with respect to any given request might be minimal or non-existent.
Step 3: Assuming you are subject to the CCPA and the request is from a legitimate source, you’ll need to respond and fulfill the request. How you respond depends on your business’ unique circumstances.
Ok, so how do I know if my business is subject to the CCPA?
Easy. If your company is (1) a for-profit and (2) you either:
- have revenues higher than $25 million a year; or
- get (or give out) personal information on 100k California residents a year; or
- make more than half of your money by selling California residents’ personal information a year
…your company is subject to the CCPA and you need to have workflows in place to comply with it (assuming you actually do receive personal information from California residents of course – if you’re a mining company in South Africa, for example, you might be ok).
(C) above is pretty edge-case, that’s for legit data brokers and companies in AdTech / MarTech. If you meet (c) as a requirement you probably aren’t reading this article because you already know all about the CCPA.
(B) above is less rare but if you’re moving that amount of data around you’re probably quite a large business.
(A) above is probably the broadest net. A lot of companies will be snared by that, and many of them might not even realize it.
Also, at the risk of getting into too much detail, I will also mention that the CCPA applies to companies that are subsidiaries or affiliates of other companies to whom the CCPA applies, as well as companies who share common branding with such a company.

Are B2B businesses in-scope?
Yes. There used to be an exemption but it expired Jan 1, 2023. There is plenty of confusion on thus subject.
What is a “consumer?”
“Consumer” means a human being who is a California resident (i.e., they currently live in California). I know, it’s a little misleading because it sounds like it’s only for B2C companies, but it’s not.
What information is in-scope (what’s “personal information”)?
It’s broad, like really broad. Don’t think “social security numbers”, think “yeah pretty much everything.” To be exact, “personal information is information that identifies, relates to, or could reasonably be linked to a particular consumer or household. For example, it could include a consumer’s name, email address, records of products purchased, internet browsing history, geolocation data, fingerprints, and inferences about the consumer’s preferences and characteristics.”
What kind of requests can people send under the CCPA?
They can request a bunch of different things, including to:
- Delete personal information collected from the consumer
- Access their personal information collected by the business
- Correct inaccurate personal information
- Opt-in to a financial incentive program
- Opt-out of the sale of their personal information
- Opt-out of the sharing of their personal information
- Limit use and disclosure of sensitive personal information collected or processed by the business for the purpose of making inferences about them
- Know about the information collected about them, how it’s used, and how it’s shared with others.
How do I know if the CCPA request we received is legit or not?
You won’t know initially whether a request you received is legit. That’s why you need a process for verifying the authenticity of the request and the identity of the requester. See below for more information.
My company doesn’t sell “personal information” but maybe we “share” it. What does “sharing” mean under the CCPA?
Pretty much any transfer to anyone else. It’s defined as “sharing, renting, releasing, disclosing, disseminating, making available, transferring, or otherwise communicating orally, in writing, or by electronic or other means, a consumer’s personal information by the business to a third party…”
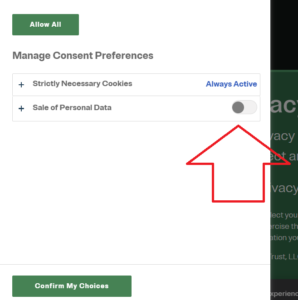
What’s up with these “do not sell or share my personal information” links on websites nowadays?
They are required by the CCPA for businesses that are subject to the CCPA. Plenty of companies that should have those hyperlinks on their webpage’s footers do not, likely from ignorance of the law.
Why are people running bots that spam CCPA requests?
I’m not sure, but I am guessing that doing so is some sort of opening move for a scam/scheme. Identity theft, for example.
How do I not go broke dealing with all of these inbound CCPA requests?
You need to design a workflow to handle them that is effective at filtering out the invalid requests. Then, add some automation where possible. For example, a simple and low-tech workflow might look like this:
- “Do Not Sell or Share My Personal Information” hyperlink added to footer of homepage
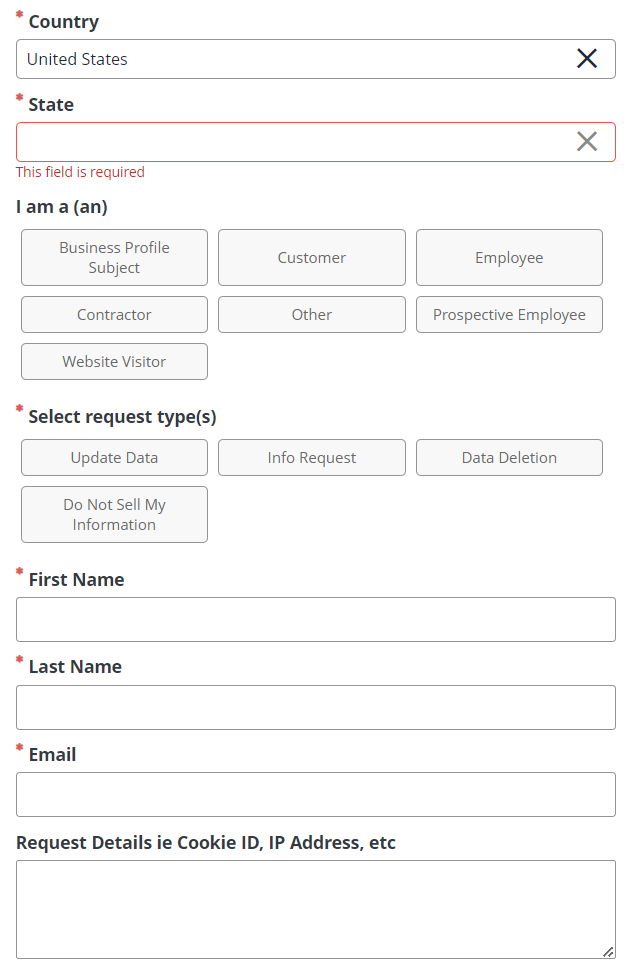
- Links to a web page with a web form and reCAPTCHA. The form has fields for first name, last name, email address, country of residence, state of residence, and a text field for the end user to describe their request. The reCAPTCHA should filter a lot of the spam from bots.
- Acknowledgment. Email dispatched acknowledging receipt of request and letting the end user know that their request will be reviewed.
- Backend: the web form should populate a data table on the backend – each row should be supplemented with a date and time stamp and an IP address
- 2 workflows should be documented and implemented, one to verify the authenticity of the requestor and another to fulfill the request itself once authenticated (Section 7060).
- Opt Out of Sale/Sharing Requests. You skip identify authentication here because it’s actually prohibited by the CCPA. Proceed right to Fulfillment.
- Other Requests (e.g., delete, correct, know). You need “reasonable security measures to detect fraudulent identity-verification activity and prevent the unauthorized deletion, correction, or access of a consumer’s personal information.” This workflow should follow any of the business’ established identify verification workflows. For example, you might note the country that corresponds to the IP address. If the request is coming from a non-U.S. IP range you could ask for an explanation from the requestor. You could also ask the requestor to provide further information (stuff they didn’t put in the web form) that only the authentic person would know, such as “approximately when did you originally open an account with us?” If identify can’t be verified, a rejection email should be sent.
- This workflow is going to depend both on the type of request received and on the individual facts and circumstances specific to the business receiving the request. There are a few more niche, edge-case rules in the CCPA that come into play here, such as the fact that deidentified information is an exception to these requests.
CCPA compliance is a lot of work, how do I streamline it?
Once you have a serviceable workflow and dataflow in place, consider automating aspects of it. For example:
- You can have different workflows for cookie vs. non-cookie requests.
- “Sale and sharing” can happen via third-party cookies or some other process. A lot of companies use tools like OneTrust to provide toggles to permit the end user to turn off sale and sharing via third-party cookies.
- For non-cookie sale and sharing, you often see a web form or simply a hyperlink to an email address, such as DPO@[companyname].com or privacy@[companyname].com.
- You could block web from submissions on your CCPA request web page if the IP address doesn’t correspond to the U.S., with the resulting error web page instructing the end user that, if they think they received the block in error, they should either (i) turn off their VPN and/or (ii) email the Data Privacy Officer (provide an email address for a workaround).
I’m still confused, can you just summarize the CCPA requirements incumbent upon businesses?
Summary of CCPA Obligations
- Privacy Policy. Must publish a Privacy policy and it must include a ton of detailed information about the type of personal information collected, the purpose of collection, and the sourcing of collection, as well as instructions on how individuals (California residents) can submit CCPA requests (Sections 7010 and 7011).
- Opt-Out Hyperlink. IF you sell or share personal information: a business that sells or shares personal information shall provide a Notice of Right to Opt-out of Sale/Sharing or the Alternative Opt-out Link in accordance with the CCPA (Section 7010) on the homepage’s footer (or header) (Section 7013 and 7015).
- Workflows. Must have a workflow/process for handling requests, including both identify verification as well as request fulfillment.
- Deletion Request Daisy Chain. Process for flowing down CCPA requests to vendors (“as well as to pass deletion requests not only to service providers but also to contractors and third parties to which the businesses have sold or shared information”) (Section 7053(3)). “Right to delete: You can request that businesses delete personal information they collected from you and tell their service providers to do the same, subject to certain exceptions (such as if the business is legally required to keep the information).”
- Internal policies and procedures for compliance (“including requirements related to data retention, data minimization, and purpose limitation…”)
- Sensitive Personal Information. If you process this type of information, which is a subset of “personal information”, you need a separate notice for it (Notice of Right to Limit) (Section 7014). Sensitive Personal Information is things like consumer’s social security, driver’s license, state ID card, passport number, racial or ethnic origin, religious or philosophical beliefs, sexual orientation, union membership, biometric information (fingerprints, retina scans), and genetic data.
- Other, more edge–case requirements under certain circumstances (these don’t apply to everyone), such as when providing financial incentives to consumers (the requirements around which echo some of the prohibitions around Bundling under GDPR), or standing up training and recordkeeping (Article 8).
What about CCPA obligations for unstructured data?
The CCPA actually does provide businesses with some relief around hunting down every last piece of personal information in their systems. These exceptions are being referred to as the “disproportionate effort” provisions and they basically say that if hunting down certain personal information would take too much effort, the business doesn’t have to do it but they do have to explain this in detail to the requestor (see, for example, Section 7024(h)). Section 7001 also has a detailed definition of “disproportionate effort.” 7001 also defines unstructured data as “…personal information that is not organized in a pre-defined manner and could not be retrieved or organized in a pre-defined manner without disproportionate effort on behalf of the business, service provider, contractor, or third party.”
How should we verify identity for CCPA requests?
The CCPA requires identity verification for some types of requests (see above – know, delete, correct). There is no one-size-fits-all answer to identity verification approach. One consistent rule is that businesses should avoid asking for brand new personal information to be disclosed to them as part of the verification process (stuff they don’t already have on file) because this just creates additional personal information they now need to track (and operationalize CCPA compliance for).
Businesses should evaluate their own situation to determine the best approach. For example, perhaps all personal information is only received if an end user has an account and access is gated by authentication (MFA, username/pw, etc.). The business might then require the requester to log in to their account to prove who they say they are and submit the CCPA request from within the account itself (a non-public web page).
There are entire white papers written on identity verification and entire industries and tools associated with the concept – it’s not a new thing that came around as part of the CCPA or CPRA.
What’s the CPRA and how is it different from the CCPA?
The CPRA is the California Privacy Rights Act of 2020. It rewrote portions of the CCPA and added new portions. The CPRA took effect on January 1, 2023, applying to personal data collected on or after January 1, 2022. Think of it like an update to the CCPA. When folks refer to the CCPA nowadays it’s safe to assume they are referring to the CCPA as updated by the CPRA, unless they clearly indicate they are referring to the original version of the CCPA.
How is the CCPA different from GDPR?
The CCPA is not California’s equivalent of the GDPR. There are many, many differences and a complete answer here is impossible, but there are plenty of decent summaries of the similarities and differences on the internet. Perhaps the most important thing for businesses to understand here is that some of the internal controls, workflows, training, and policies that were created and operationalized to facilitate GDPR compliance can be leveraged, with sufficient supplementation and changes, to also facilitate CCPA compliance (for example, sign-up web form design that avoids Bundling under GDPR). In other words, it may not be necessary to start from scratch.
How long does a business have to respond to CCPA requests?
It depends on the type of request. For requests to delete, know about, or correct, businesses must acknowledge the request within 10 business days and fulfill it within 45 calendar days. For requests to opt-out of sale and/or sharing, fulfillment must be performed no later than 15 business days from the date or receipt of the request.